De-Risk your Identity Program
Know your IAM Maturity Score by identifying strengths and opportunities with IAM experts.
De-Risk your Identity Program
Know your IAM Maturity Score by identifying strengths and opportunities with IAM experts.
IAM maturity is essential for organizations to protect digital assets and ensure seamless operations. An immature IAM program not only exposes you to cyberthreats and compliance risks but also hinders progress in strengthening security posture, managing audit and risk, and enhancing operational efficiency. Prioritizing IAM maturity is crucial for mitigating security risks and streamlining compliance processes.
Ready to enhance your organization’s security and efficiency? Learn how our IAM Maturity Advisory Program can help you achieve your goals.
IAM maturity is essential for organizations to protect digital assets and ensure seamless operations. An immature IAM program not only exposes you to cyberthreats and compliance risks but also hinders progress in strengthening security posture, managing audit and risk, and enhancing operational efficiency. Prioritizing IAM maturity is crucial for mitigating security risks and streamlining compliance processes.
Ready to enhance your organization’s security and efficiency? Learn how our IAM Maturity Advisory Program can help you achieve your goals.
Simeio’s Identity Access Management Maturity Advisory Program (IAM MAP) is entirely focused on your people, processes, environment and technologies supporting Identity and Access Management. Through this in-depth one-day workshop, our joint teams will identify gaps and prioritize areas requiring maturity improvement.
The IAM MAP helps prioritize performance improvement strategically and drive IAM maturity, resulting in stronger overall security for employees and customers.
How It Works
Your advisory begins with a one-day knowledge sharing session about the eight levers of IAM maturity, providing strategic risk management context for your business.
Participants are guided through a comprehensive questionnaire. The foundation provided by this session enables you to extract greater value from the assessment and embeds IAM maturity knowledge into the process going forward.
To get the most out of the workshop, we recommend the following stakeholders be involved:
- AD & Cloud Teams
- Architects
- Business Application Owners
- CISO
- Compliance / Internal Audit
- Help Desk
- Human Resources
- IT Networking, Security, Infrastructure & Telecom
Taking Action
Within a week, we produce a summary presentation of our recommendations and provide you with additional materials and tools we think will be helpful.
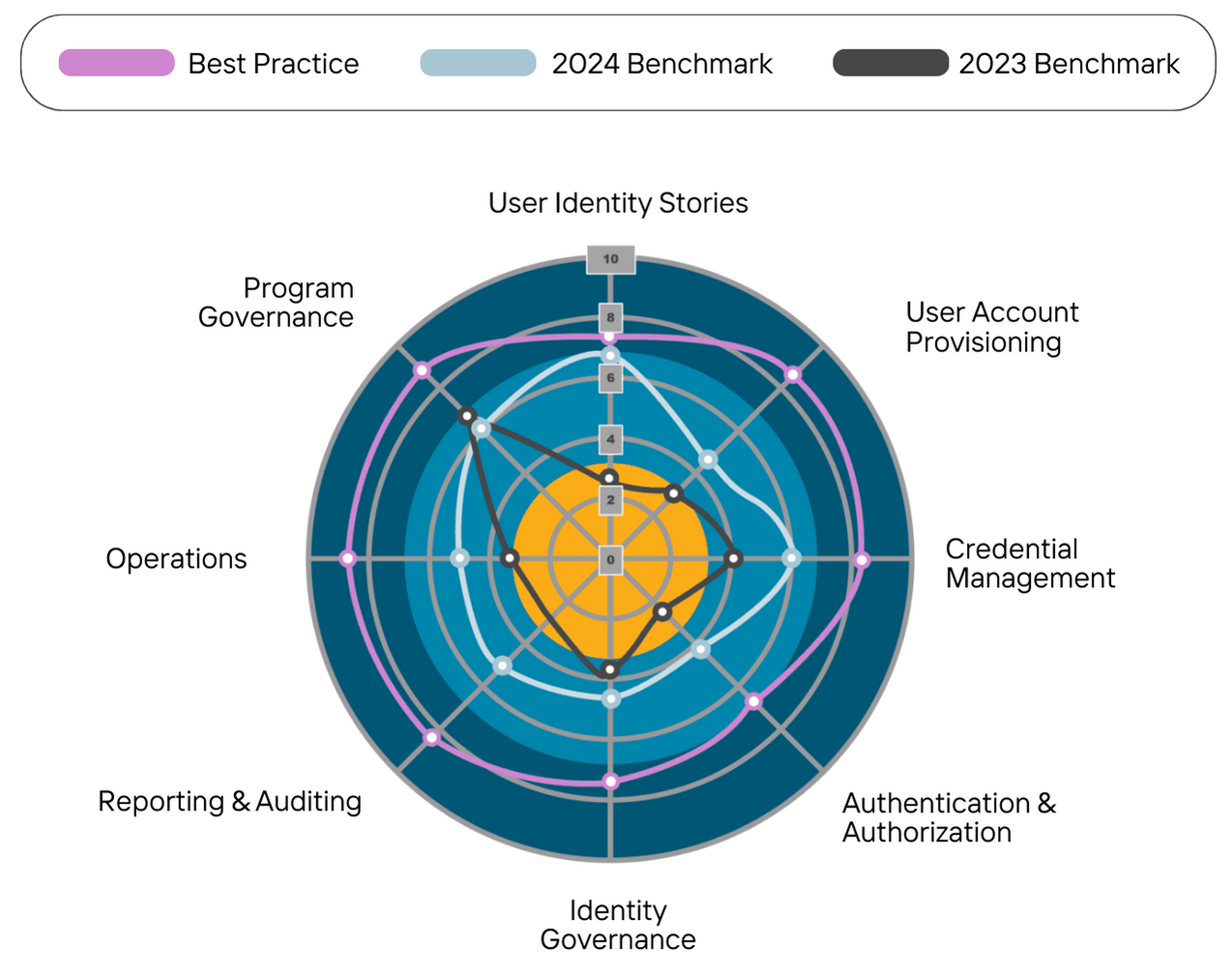
You’ll also receive an implementation plan which prioritizes the sequence of events, in priority order, at a detailed level. You’ll retain access to the online benchmark so you can remodel the value of your IAM program at any time and as often as you like. Our clients use this as their scorecard and progressively push maturity up by increasing their score across the 8 Levers and 80 Measures.
Taking Action
Within a week, we produce a summary presentation of our recommendations and provide you with additional materials and tools we think will be helpful.
You’ll also receive an implementation plan which prioritizes the sequence of events, in priority order, at a detailed level. You’ll retain access to the online benchmark so you can remodel the value of your IAM program at any time and as often as you like. Our clients use this as their scorecard and progressively push maturity up by increasing their score across the 8 Levers and 80 Measures.
Discover the 8 Levers
User Identity Stores
- How many employees and non-employees work at the company?
- How effective is the process for onboarding/off-boarding non-employees, and what provides the repository for managing their identity data?
- How many redundant copies of user identity data create risks and inefficiencies for IT and business stakeholders?
User Account Provisioning
- Do new employees wait around on Day 1 and longer for access?
- Does a centralized security team have control over access to your key systems and applications?
- Do you know how many orphan accounts are in your key systems or applications? (Accounts without owners or service accounts no longer needed)
Credential Management
- Is your company leadership prepared for an enterprise-wide password reset event?
- Does your company have a standard password policy that is enforced across all key systems and applications?
- How many people see the information when you issue new login credentials?
Authentication and Authorization
- How does the enterprise provide SSO for non-AD-based applications?
- What percentage of your key applications require MFA for login security?
- How does the enterprise manage authentication for cloud or SaaS applications?
Identity Governance
- How do you manage Access Certifications for all your key systems and applications?
- What percentage of your applications are governed by a centralized process?
- Does your organization perform account entitlement analysis and role mining?
Reporting and Auditing
- Do you have the skilled resources required to properly support and manage your IAM solutions?
- Does the IAM team follow a standardized change management process?
- Does the IAM team adhere to agreed-upon SLAs for all IAM systems?
Operations
- Do you have the skilled resources required to properly support and manage your IAM solutions?
- Does the IAM team follow a standardized change management process?
- Does the IAM team adhere to agreed-upon SLAs for all IAM systems?
Program Governance
- Does the IAM program operate from a well-organized, long-term strategy and roadmap, and are key metrics tracking progress against the roadmap?
- Does the IAM steering committee (formal or informal) support the program priorities and work to resolve organization resource conflicts?
- Has the IAM or Security Architecture leader developed an IAM Reference Architecture, with associated standards, and are these enforced across the enterprise?
Related Resources

IAM Maturity
Elevate your Identity and Access Management systems from Ad Hoc to Optimized through Simeio’s Maturity Model. We standardize the path to excellence in identity.

IAM Maturity Benchmark: Is Your Business’ Identity Security Too Immature for 2024
Without a solid action plan, the implementation of meaningful changes to an enterprise’s identity fabric can seem an insurmountable challenge.

Infographic – 8 Components of IAM Maturity Assessment
IAM Maturity is crucial to understanding the state of your Identity program, but what goes into it? Learn the 8 building blocks of a comprehensive and meaningful IAM Maturity measurement.