
The Third Industrial Revolution propelled the growth of computers, machines, electronics and internet in an industrial setting. The Fourth Industrial Revolution (4.0) propelled by the next phase of digital transformation of the manufacturing sector is giving rise to many disruptive trends. These include mechatronics, advances in human-machine-interface (HMI), data science/analytics, the Internet of Things (IoT), and enhanced connectivity with enterprise level systems in complex environments.
As part of the 4th Industrial Revolution, manufacturing enterprises are investing in disruptive) infrastructure to enhance productivity. This involves adding tools and hardware (i.e., machines) that can automate and communicate within their production lines. Whether to scale up operations or improve upon existing pipelines, these machines fit into the larger complexity of the enterprise’s grand apparatus.
But in the modern day, these machines are not connected only by levers, hydraulics, and power cables. They are also digitally linked to marvelously intricate computer systems within cloud and hybrid environments that centralize and streamline controls. In the factory of modernity, machine identities are gaining importance and have become a very critical component of this apparatus. Yet, too often, they are also woefully neglected as a consideration until disaster strikes.
Similar to humans, machines use digital credentials to authenticate and communicate within the network. The management of machine identities (also known as non-human identities / NHI) in an industrial setting becomes crucial to ensures that integrity, confidentiality and security of data which is paramount to operations and to protect the underlying IT systems while ensuring productivity.
What are Machine Identities and How are They Managed?
In order to manage machine identities, let’s look a understanding machine identities – Machine identities, analogous to human identities, are unique identifiers and keys (cryptographic) which are used to perform functions such as authentication and authorization. within the network for various applications, devices, and services. Similar to human identities, machine identities need to be secured from unauthorized access to ensure security and integrity of the enterprise infrastructure.
Machine identities originate from IoT devices which have an identity attached to them, virtual machines (VMs), applications (service accounts), bots built from robotic process automation (RPA), multi-cloud environments, smart buildings, fleets for logistics, self-driving vehicles, or any other form of automation and services. Compared with human identities, which comprised of employees, business partners, customers, vendors, third-party consultants, etc. Machine identities pose a bigger threat than human identities.
Machine identities interfacing with key enterprise systems can be the gateway to breach privileged and sensitive data in an organization. A study conducted by CyberArk, a leading identity management and protection platform, states – Nearly three-quarters (68%) of respondents indicate that up to 50% of all machine identities have access to sensitive data, compared to 64% who report that about half of human identities have access to sensitive data.” This is a result of the rapid growth of machines, causing an exponential growth in identities within an enterprise.
The global machine identity management market is expected to grow at a CAGR of 12.1% to approximately US 38 billion by 2031. This is primarily driven by advancements in the adoption of cloud-based models, proliferation of automation technologies and their use cases, infrastructure-as-a-code (IaaC), edge computing, adoption of blockchain technologies and growing usage of artificial intelligence (AI).
Machine secrets have often been exposed in code repositories, which makes also the reason they appear in the dark web. A real-world example is the 2022 Uber breach which took down many of its internal communications and engineering systems through a social engineering attack. This was possible as the hacker gained access to Uber’s systems.
Machine identities today have become very crucial within the evolving digital landscape due to rapid increase in connected devices, and services that are emanating from digital transformations which employ Internet of Things (IoT), cloud computing models and microservices architectures. Machine identities today are a key portion of IT, cybersecurity, and zero trust strategy and are well integrated into the overall IT infrastructure. To build trust and secure machine-to-machine communications, it is key to establish access controls to protect the infrastructure within a manufacturing organization.
Machine Identity Lifecycle Management
It becomes imperative to ensure that machine identities follow a similar process of lifecycle management and protection like human identities. Unauthorized access to machine identities in a manufacturing environment can prove detrimental to the overall operations and compromise organizational secrets and infrastructure, leading to huge capital and reputational losses. This is why it is very important for manufacturing organizations to keep a holistic view of all machine identities, their interactions within the enterprise network, associated risks and vulnerabilities, and appropriate disaster recovery and business continuity plans.
With the exponential proliferation of machines, standardizing processes and centralizing machine identity management utilizing automation, audit and governance including activity monitoring, employing principles of zero trust security, just in time access (JIT) and least privilege, machines can be secured against potential cyber threats. Like solutions employed to manage and protect human identities, a comprehensive solution is the need of the hour to manage and protect machine identities and reduce the attack surface.
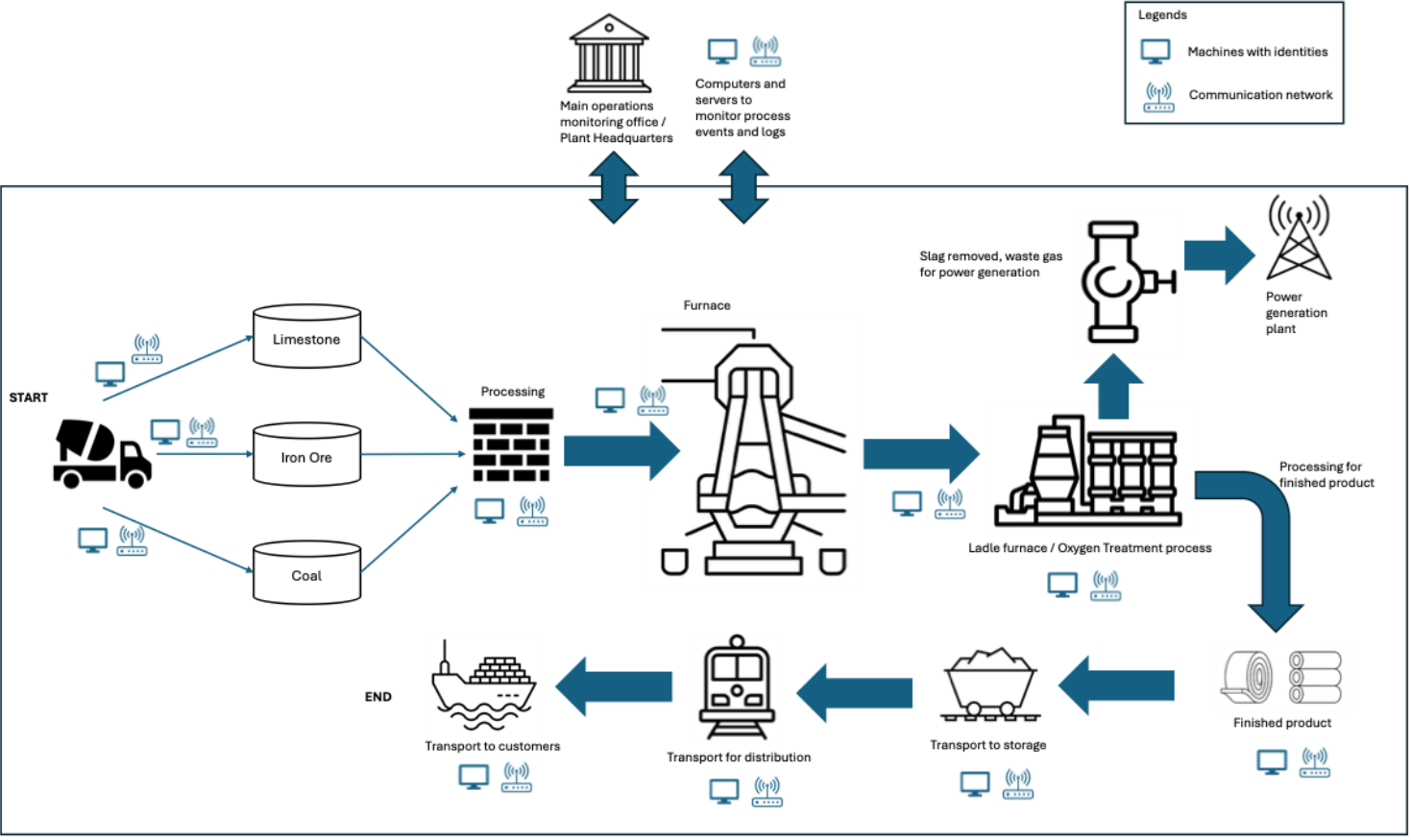
Machine Identity Management in Manufacturing
To understand machine identities in a manufacturing setting, we must dive deeper into the workflow of a manufacturing organization. We will use the example of a steel manufacturing firm. Referring Figure 1 below, which denotes a high-level process within a steel manufacturing entity, from arrival of raw material to shipping of finished good. At each step, there exist machines that communicate over a network, carrying operational data and control signals to execute processes in the overall value chain. Each machine within the network is an individual point of failure and can halt operations if compromised leading to financial and reputational damage.
Similarly in an energy grid, multiple such identities exist for machine-to-machine communication. This network of machines comprises of the “Attack Surface” which needs to be protected from external threats and actors.
Energy grids are comprised of machines within primary and secondary substations interacting through Supervisory Control and Data Acquisition (SCADA)-based systems, voltage generators, smart grid gateways, load balancers, which in turn are responsible to supply energy to business and residential customers. Each business and residential customers have smart meters that interact with the energy grid, indicating the large breadth of attack surface and exposing multiple vulnerable points for threat actors. A lot of focus is laid on protecting the grids (primary and secondary substations), and very little emphasis is placed on protecting the business and residential customer meters.
It is important that the grid architecture of a city is holistically considered while designing overall cybersecurity measures to minimize the attack surface and eliminate any vulnerable points of attack. A key reason for grids from utilizing the best in breed cybersecurity technologies is the age-old infrastructure (i.e., legacy) which needs to undergo modernization. Energy firms utilize SCADA networks to control their industrial systems, which need to be updated to protect themselves from growing cybersecurity threats. E.g., A successful ransomware attack in 2021 on the 2022 Colonial Pipeline provided a window into the vulnerability and the many attacks points via the cross-pollination of IT and SCADA networks. The attackers disrupted the supply of oil supplies on the US east coast and demonstrated the lack of a cybersecurity framework for both preparation and incident response.
Similarly, there are multiple examples of cyber-attacks in manufacturing firms, where machine identities have been compromised. E.g., Norsk Hydro, an aluminum manufacturer with operations in 40 countries, in 2019, was forced to close multiple plants after a ransomware attack from a software called LockerGoga, which damaged IT systems across business functions including their smelting plants in multiple countries. The underlying details of the attack remain unclear, but it is believed that credentials were sourced from the dark web or sourced through a prior phishing attack. The overall disruption in operations impacted the earnings of Norsk Hydro. Renault-Nissan was also a victim of cyber-attack in 2017. The WannaCry ransomware attack disrupted production in multiple plants world-wide with estimated losses in billions.
Reach out to a Simeio representative now and start charting out your roadmap to an optimized identity roadmap.
Written by Rahul Purohit

