
ITDR, or Identity Threat Detection and Response, is a comprehensive security strategy focused on safeguarding identity systems from various threats and vulnerabilities. It integrates multiple security disciplines to detect, investigate, and respond to threats targeting identity infrastructures.
So, what are the key components to ITDR and the threats that may occur? Furthermore, what are the current recommendations to make sure you are as protected and aware as possible?
Key Components of ITDR
Tools: ITDR uses identity and infrastructure security tools such as Access Management, Identity Governance and Administration (IGA), Privileged Access Management (PAM), and Multi-Factor Authentication (MFA). Additionally, it employs Infrastructure Security tools like Network Detection and Response (NDR), Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and Security Orchestration, Automation, and Response (SOAR).
Threat Intelligence: This involves ensuring that IAM (Identity and Access Management) controls and processes are functioning effectively. Staying aware of potential threats and irregularities in identity processes is essential to keeping infrastructure secure.
Processes: ITDR aims to identify and fix failed events or processes in IAM. This may include auto-healing of IAM processes to maintain system stability and security.
Best Practices: This ensures that all sensitive and critical applications are protected by MFA, that Role-Based Access Control (RBAC) is enforced, and that orphaned accounts (unused accounts still active in the system) are promptly removed to minimize risks.
Knowledge Base: A good ITDR leverages best practices and industry standards to evaluate the maturity of IAM programs. This includes tracking how well an organisation is doing against established IAM benchmarks.
Threats Addressed by ITDR
There are many threats to any modern business. The first are Security Gaps, such as shadow access (unauthorized or hidden access). Next are vulnerabilities such as unmanaged, misconfigured, or exposed identities. Finally, there are compromised identities whereby compromised credentials can be used unseen as if by the originally intended user. Other threats generate around access flows and the way users cross to and from other applications and the access issues this may create.
Active attacks are those that we traditionally imagine when we think of a ‘cyber-attack’. These include man-in-the-middle (MitM), impersonation, and session hijacking. Finally, lack of estate visibility and the presence of unknown SaaS apps may pose open threats and security risks.
Use Cases
Identity Security Posture Management: Continuous monitoring and analysis оf identities, access rights, and authentication processes throughout an organisation’s ecosystem.
Identity Incident Investigation & Response: Identifying, containing, and removing threats to identities, followed by recovery and mitigation strategies.
Identity-Based Zero Trust: Implementing and overseeing strong identity management practices, such as continuous verification of user identities and privileges in a Zero Trust framework.
Secure Privileged Access: Using PAM solutions to mitigate risks associated with privileged accounts and ensure compliance.
Identity Governance Controls: Establishing governance frameworks to minimize risks related to unauthorized access, data breaches, and compliance violations. In summary, ITDR represents a comprehensive approach tо identity security by integrating tools, processes, and best practices. This serves to address identity-based threats and provide robust governance. It also ensures a more resilient and secure identity infrastructure.
The ITDR Approach to Incidents
Below is an example of a 4 step, high level process on managing incidents:
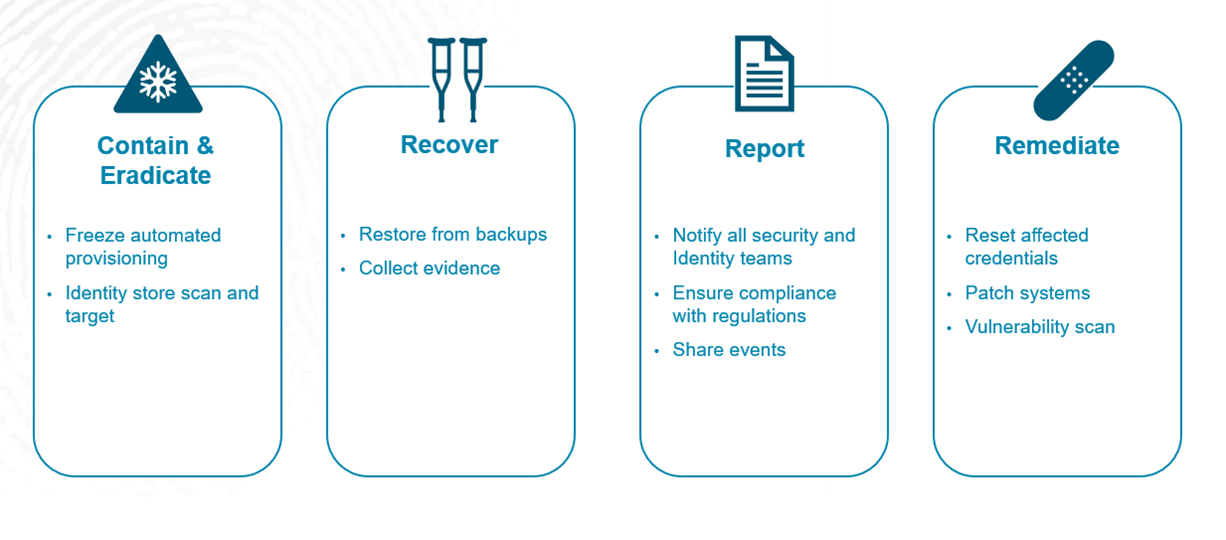
ITDR implementation forms a critical segment of your enterprise’s risk posture. Without sufficient provisions for threat detection, you won’t know that your systems are compromised until it’s too late. In the next blog in this series, you will learn how an optimal ITDR solution can be implemented.
Written by Daniel Le Hair

