Addressing privileged access is one of the key requirements of a mature identity fabric. A strong privileged access solution enables swift remediation of emergent security risks. Conversely, an exposed and vulnerable PAM solution endangers a whole enterprise. If the PAM is breached and brought under the control of bad actors, their potential damage becomes catastrophic. As such, addressing privileged access as both a necessary yet potentially dangerous identity pillar serves as a chief concern for identity professionals and company stakeholders.
The infographic below gives you a good basic understanding of PAM (Privileged Access Management). It covers important concepts that are key to understanding PAM’s role in managing identities.
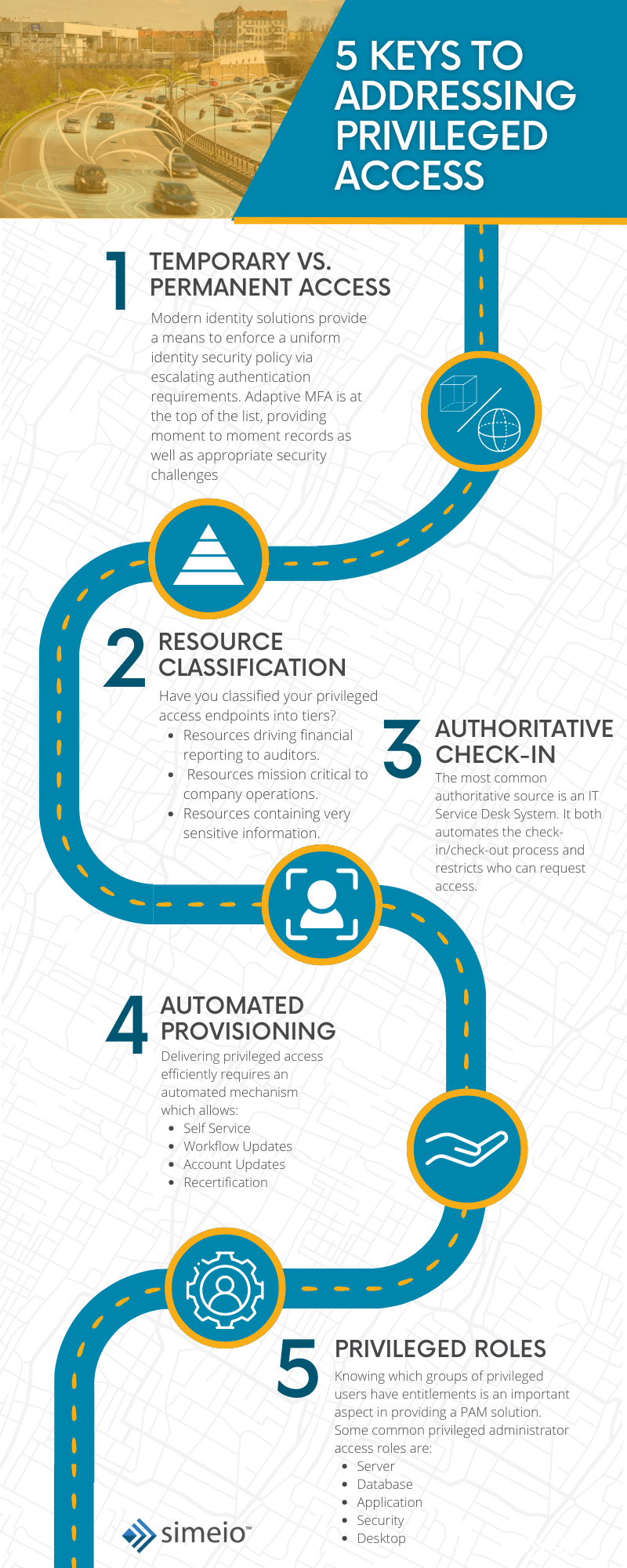
Your Keys to Addressing Privileged Access
- Access: Temporary vs. Permanent – Modern identity solutions help enforce a uniform identity security policy through escalating authentication. Adaptive MFA tops the list, providing moment-to-moment records as well as appropriate security challenges.
- Classification of Resources – Enterprises must classify their privileged access endpoints into tiers if they hope to compete against modern hackers. These resources can be broken down into three main types. These are those driving financial reporting to auditors, those mission-critical to company operations, and those containing very sensitive information.
- Check-in Authority – The most common authoritative source is an IT Service Desk System. It both automates the check-in/check-out process and restricts who can request access.
- Automation of Provisioning – Delivering privileged access efficiently requires an automated mechanism which fulfills several functions. These include self service, workflow updates, account updates, and recertification.
- Roles and their Privileges – Enterprises need to know which groups of privileged users have entitlements. Some common privileged administrator access roles are: Server, Database, Application, Security, and Desktop.
Addressing PAM with Simeio
Understanding the state of your privileged access solution is key to improving upon it, and no better starting point exists than a Simeio identity maturity benchmark. This world-class assessment process provides your enterprise with an actionable breakdown of your cybersecurity, audit readiness, and automation processes, all crucial to addressing privileged access.
Contact an identity expert now and schedule your benchmarking appointment now.